How secure is your network from penetration? Most often it is not as secure as organizational leadership believes. Tuearis has some of the best Certified Ethical Hackers on staff to find out the truth to this question.
Test Your Security
Perhaps you have security personnel on staff and want to test their preparedness, or maybe you have trusted your organization’s security to an outside cybersecurity business. Either way, we can work with your business leaders to perform a Penetration Test that will let them see how a real attack could penetrate into the network and put the business at risk.
Black Box and Other Options
Penetration Tests come in several varieties depending upon the desires of the organization. One type is referred to as a “Black Box” wherein the attacking team is given little to no information on the environment or security that is in place and is expected to find a way in. Tuearis Cyber offers this type of testing, as well as others, to truly put your security team to the test. Our Certified Ethical Hackers (CEHs) are among the best in the business and have experience across many industries, as well as government and private sectors.
Helpful Reports
Tuearis will provide a detailed report and helpful tips for improving your security after the Penetration Test is completed. This report is where your team improves and your organization becomes more secure.
Are you ready to be put your security to the ultimate test? We are here to help. Tuearis Cyber is your Security. Tested.
Proper IT operations are costly, creating unnecessary strain on most businesses. We eliminate the need for expensive hardware, electrical, cooling and experienced labor – you reap all the benefits of quality IT without the mess. Reduce operating expenses while delivering superior solutions.
PCI, ISO, HIPAA, FISMA – we have it all. Maintaining proper security compliance can be critical to many businesses. Tuearis ensures your company is properly services and maintained to Industry Best Practices and International Security Standards.
From Digital Intellectual Property to Physical Property, company assets come in many forms. Whether you’re tracking a lost device and wiping it for security, or wish to ensure your property is only accessed by authorized personnel, ensuring the security of these assets is critical to every business.
Greater Security – Security Experts with experience in many environments under senior leadership that have seen it all await you in our Security Operations Center. Your Security Team in the Tuearis SOC is uniquely positioned to leverage their collective cybersecurity knowledge from many industries, public and private sectors, and enterprise down to small business, in order to secure your business!
Save on CapEx – The capital expense to stand up a SOC is a tremendous up-front hit to many businesses. However, we can roll you into the Tuearis SOC for far less!
Get rid of the Stress – Deploying unfamiliar technologies and stumbling through the initial design and maintenance of these important cybersecurity tools will most likely cause business operators a great deal of stress. What if you were to rid yourself of that stress and entrust the work to a Security Team that does it all of the time?
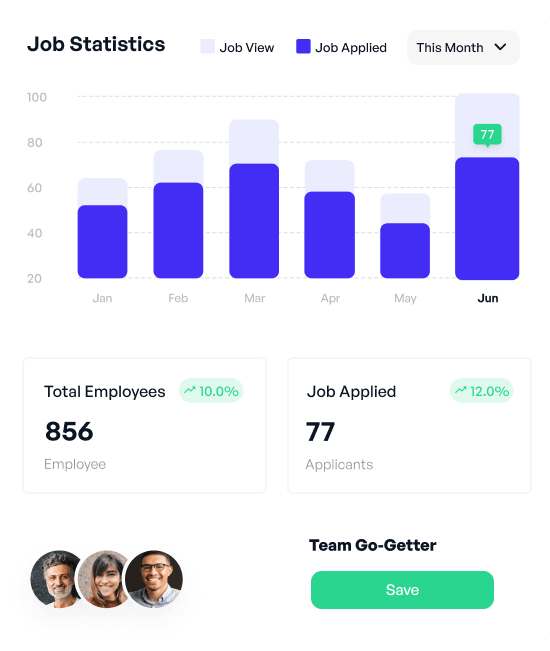
Remove Staffing Woes – Beyond initially hiring SIEM and SOC professionals, keeping your Security Team staffed and happy is an ongoing work that you could outsource altogether!


The team at Tuearis has experience deploying at maintaining SIEM and SOC with every size of business and is trusted by major corporations including several Fortune 100 companies with this essential and complicated technology. We have worked with some of the nation’s largest transportation companies, the Department of Defense, software companies, state governments, and service industry leaders on these very technologies.
Tuearis also has:
SIEM experience in some of the world’s most complicated environments
100% Continental U.S. SOC with the ability to meet any regulatory requirements
IBM’s QRadar SIEM, Gartner’s leading SIEM technology
Predictable costs allowing you to control your Operating Expenditures
An experienced staff of Security Professionals
Customized offerings to design the perfect SOC for you
Partnerships with the leading SIEM technologies
Experts in each SIEM technology we deploy
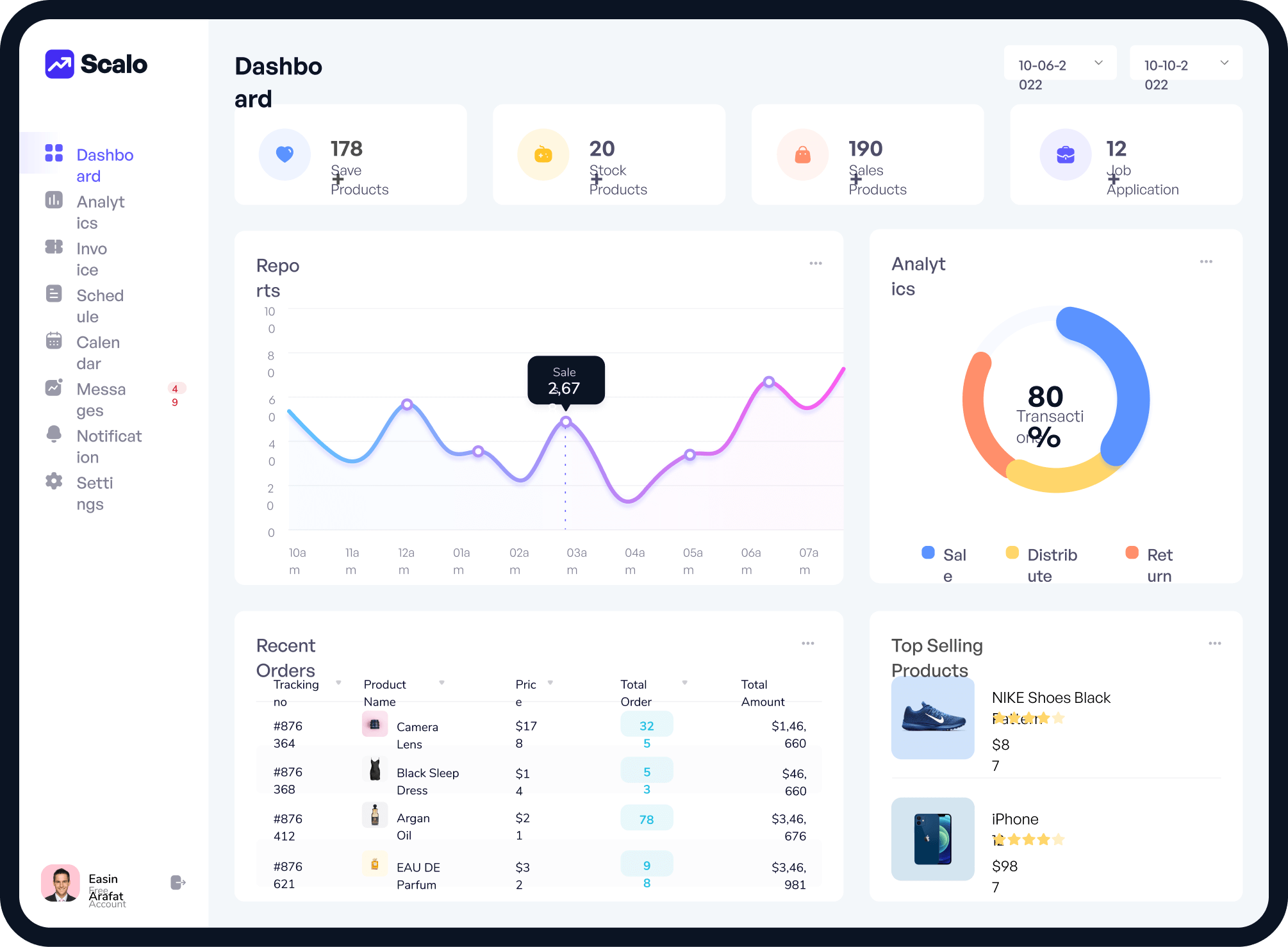
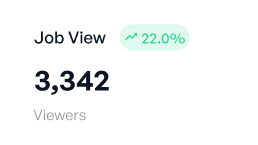
Businesses have different needs from a Security Operations Center.
Which technologies are best for your environment?
What type of monitoring fits your security needs and budget?
What policies should be in place to protect your business operations?
Security Operations Centers should not be a “one size fits all” solution. If you use Tuearis Cyber, your SOC will be tailored to your business needs in every way.
We are not technology resellers; We are your Security Staff.
We will help you identify which technologies would work best for your environment by factoring in the current environment, growth projections, and needs. Our team is also constantly on the lookout for new and better technologies to weave into our Technology Stack so your cybersecurity will always be on the cutting edge.
24×7 SOC
Live Monitoring and Incident Response 24 hours per day, 7 days per week, 365 days per year
We will help you design custom Security Policies.
This is just another way that we work together with your business as a whole as your Security Staff.
Contact us today to schedule a consultation to begin planning the right SOC for your business needs!
Trust Tuearis to manage your Security Operations Center and REST SECURED.
Professional Services
Company